AmCham Kuwait held a joint webinar with the Overseas Security
Advisory Council (OSAC), and (ISC)² on ‘Enterprise Risk Management: The Relationship
Between Traditional Security and Cybersecurity.
The panelists for this discussion were Shahzad Khattak Assistant- Legal Attaché Supervisory Special Agent of the Federal Bureau of Investigation (FBI), Layth Alissa- Partner at Everyware Pro, Colin Brown- Security Management Consultant at Saudi Arabian Chevron, Richard Archdeacon – Advisory CISO for the EMEA region at Cisco, and Senthil Kumar, Managing Director – Technology Consulting, Protiviti Middle East. The discussion was moderated by Dana Winner Co-Chair at Overseas Security Advisory Council.
The purpose of the conference was to assist private sector leaders with understanding the necessity of integrating cybersecurity into risk management programs.
AmCham Kuwait’s Executive Director Paola de la Roche welcomed the panelists and moderator and welcomed (ISC)² members, OSAC Members, the U.S. Embassy of Kuwait, AmCham Members in Kuwait, Abu Dhabi, Dubai, Bahrain, Oman, Saudi Arabia, and Qatar. She then introduced Dana Winner as the moderator for the conference and discussion.
Followed by Winner discussing topics based on, Cyber aligned counter terrorism threats in the healthcare sectors and pharmaceutical industry, the relationship between traditional security and cybersecurity in the oil & gas sector, banking, as well as national and international security.
Winner stated that the purpose of this discussion was to create a better understanding of the subject of Enterprise Risk Management and bring about awareness of the crucial relationship between traditional security and cybersecurity as well as to understand that unifying both is necessary if entities want to ensure that their assets are as protected as possible.
She then invited, Special Agent Shahzad Khattak, Assistant Legal Attaché Supervisory from the FBI Legat Doha, Sub-office Kuwait to discuss on issues of national and international security.
ALAT Khattak presented on cybersecurity matters from the FBI’s perspective and spoke on the overview of the FBI’s Cyber Strategy and mission, ALAT’s role in promoting cybersecurity and supporting the overall FBI Cyber program, the importance and functions of IC3.GOV, cyber threats posed by Nation State Actors, prevention principles and private sector roles.
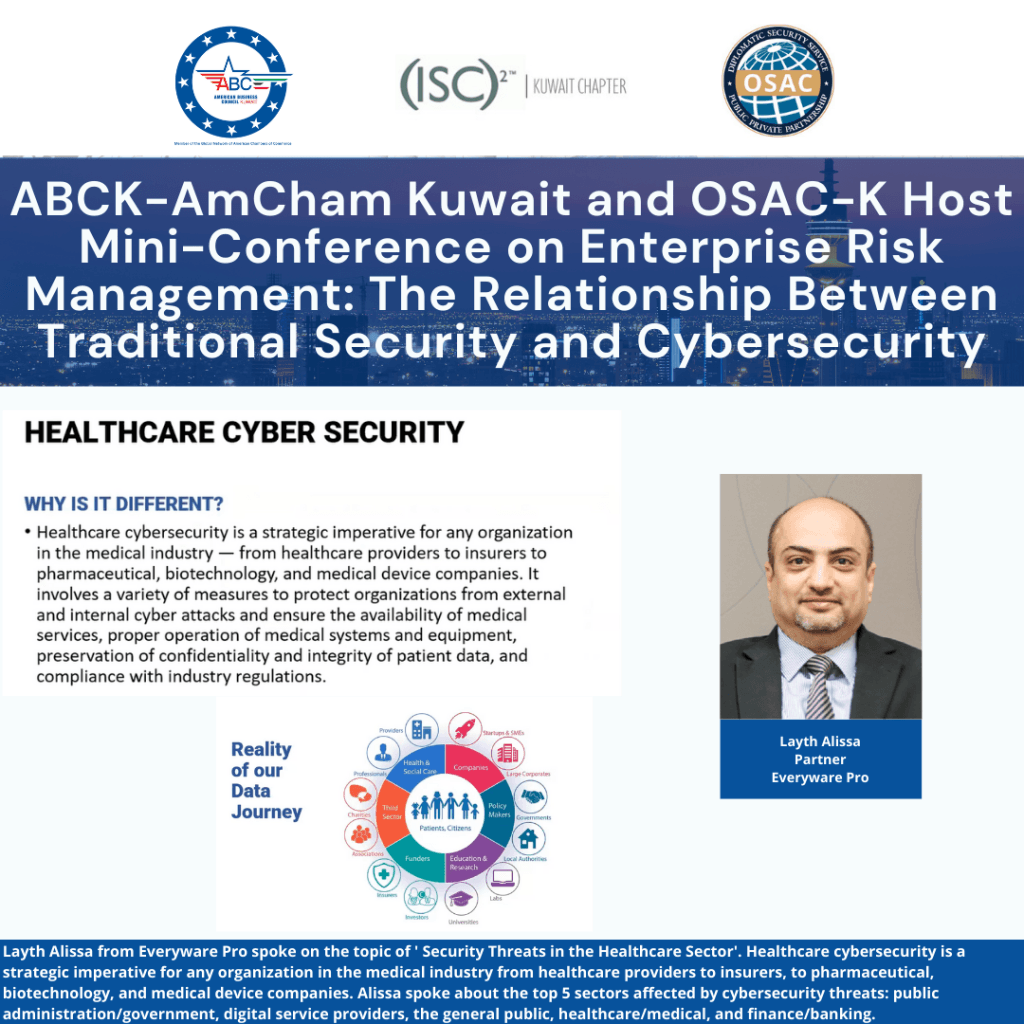
Subsequently, panelist Layth Alissa Partner at Everyware Pro, discussed the topic of
‘Security Threats in the Healthcare Sector’, as he discussed the difference in cybersecurity
within the healthcare sector, as well as ways to protect patient data along with user’s
data, inclusive of the privacy evolution.
He stated that the life sciences and healthcare industries are on the brink of large-scale disruption and the future of health will be driven by greater data connectivity and increasing consumer engagement. Protecting the safety and privacy of data is critical.
Healthcare cybersecurity is a strategic imperative for any organization in the medical industry from healthcare providers to insurers, to pharmaceutical, biotechnology, and
medical device companies, also by highlighting the top 5 sectors affected by cybersecurity
threats which include the public administration/government, digital service providers, the
general public, healthcare/medical, and finance/banking.
Alissa also stated about the Protected Health Information (Privacy Rule) HIPAA. According to HIPAA, The Privacy Rule protects all individually identifiable health information held or transmitted by a covered entity or its business associate, in any form or media, whether electronic, paper or oral.
The Privacy Rule calls this information, protected health information (PHI)”. Therefore, he provided participants ways to protect their data which included aspects of proactiveness, stopping the exposure of Google searches, not allowing copies of financial means (credit cards or KNET), not sharing any sensitive information when not necessary, asking if the clinic/hospital has self- service access. He also mentioned that inquiring about the use of external labs is important and finding out whether they share PHI such as patients Civil ID numbers or just necessary data. To finalize, he suggested to participants to never send copies of their medical files or clinical images via social media and to remember geographic boundaries, as HIPAA is not enforceable outside of the U.S.
Following the discussion, Dana Winner introduced the topic of ‘Security within the pharmaceutical sector’ by discussing the creation of the COVID-19 vaccine, and the rigorous process that goes behind its creation so that it can be used commercially.
Winner gave an overview of the clinical trial process: discovery and development, protocol creation for testing out and proving whether the discovered science has efficacy, protocol review by a wide number of scientists involved trials, regulatory review and approval, and post-marketing surveillance.
Moving on, panelist Colin Brown, the Security Management Consultant at Saudi Arabian
Chevron, addressed the topics of the ‘Relationship Between Traditional Security and Cyber
Security within the Oil & Gas sector’. Brown spoke about the first principle of cyber security
which involves: confidentiality, integrity, and availability. He compared those with the first
principle of physical security: deter, detect, delay, respond, recover, and what the purpose of each is. In his presentation, Brown spoke about risk-based planning: selection, protection, and detection, as he stated that 95% of all incidents occur due to human error, with 43% of breaches attributed to insider threats. Brown finalized his presentation by talking about the ‘industrial internet of things’: human impact, regulation, data management, GDPR, geographic spread, and interoperability.
Richard Archdeacon, Advisory CISO for the EMEA region at Cisco, also highlighted the principle of ‘Zero Trust’ and how it is applied within the oil & gas sector. He stated that the Zero Trust policy is crucial for all entities, as it questions assumptions and avoids excessive
trust being given to network management tools by default – which can be used without notice by an adversary. He went on to explain the Zero Trust principles, which are to never assume trust, always verify, and enforce the least privilege. He also detailed on how to make Zero Trust work, even within smaller organizations, by establishing trust, enforcing trust-based access, continuously verifying trust, and responding to change in trust through the prioritized incident response, orchestrated remediation, and integrated and open workflows. He mentioned that factors critical for success include a team-led approach, executive sponsorship, pilot to prove, creating demand for Zero Trust, and clear communication.
The conference was concluded by Senthil Kumar, Managing Director – Technology Consulting, Protiviti Middle East who spoke in depth about the concepts of Integrated Cybersecurity with Enterprise Risk Management (ERM) and Cybersecurity (CS) workflow framework within the banking sector as he spoke in depth about NIST publications. Kumar closed the discussion by highlighting that cybersecurity is not the responsibility of a few IT people, “cybersecurity is everyone’s job”.